Why TURN and STUN?
Most of the devices used by us are behind NAT(Network Address Translation). NAT gives private IP addresses access to the Internet. A single device say router can be act as an agent between public IP addresses and Private IP addresses with the help of NAT. A NAT device can use a single public IP address to represent many private IP addresses.
The reason behind the existence of NAT is that after 90’s the consumption of Internet grow in such a fast manner that IPs which were assigned to the host were being lost and it seemed as if the Internet growth will be stopped due to lack of IPs so the work for the solution had been started. NAT is one of the solution for this.
NAT adds an another layer of security within an organization. It hides a private network from outside world.
NAT maintains two types of IP.
1) Private IP
2) Public IP
The IP address which can be used as private IPs can be in the range of
Class A 10.0.0.0 – 10.255.255.255
Class B 172.16.0.0 – 172.31.255.255
Class C 192.168.0.0 – 192.168.255.255
We can use single public IP address to give the access to various private IP address.
We can understand this with the help of following Example
Suppose there is a PC(Personal Computer) with private IP (source address)10.0.0.1 and a server with IP 10.0.0.2.For communication when request moves to router which has NAT configured inside it,it will translate this address into public address by making NAT table.
| Source Local IP address | Source Global IP Address |
| 10.0.0.1 10.0.0.2 |
171.69.58.80 171.69.58.91 |
Table 1:NAT Table
Now the IP address of above PC is 171.69.58.80 for everyone and everyone thinks that request comes from 171.69.58.80. Similar process of mapping the IPs followed while responding to the request. The response come back to the router for the IP 171.69.58.80 as discussed above , the IP 171.69.58.80 had mapped to 10.0.0.1 so the response will move back to 10.0.0.1.
Categories of NAT:-
- Static NAT:-This is one-to-one mapping process. Suppose you want your three PCs to be connected to Internet then you have to buy three IP address for this transmission.
- Dynamic NAT:-In this there is a pool of IP Addresses. The benefit is that all the host in our network can be connected to Internet. Limitation is that the number of people who can access the Internet at a time can be according to the pool taken by us.Ex:-122.*.1.1 to 122.*.1.4,so 4 people at a time can access the Internet but all the hosts in our network can use this IP.
- NAT/PAT:-In this,single IP address can be used to provide Internet to the whole network. Service providers provide the router with this type of NAT configured into it. It is the most popular technique now a days and used in various offices.
Along with IP address NAT also translates the ports. The public address and port together is known as server-reflexive-address.
Almost for all the NAT devices (mostly home routers),any device which has the Internet connection can communicate with NATed device via sending packets to the server-reflexive-address even if they are not the receiver of the packet which initiates the connection. A source which can discover the server-reflexive address is therefore required.
Here the need of STUN and TURN server arrives!!!!!
What is STUN and TURN server?
Session Traversal Utilities for NAT(STUN) is a simple protocol which discovers server-reflexive address. STUN servers remain on the Internet and allow to check the IP and the port number of the incoming request and give response to it. This process enables a WebRTC peer to get the public IP address of the peer and establishing the direct connection.
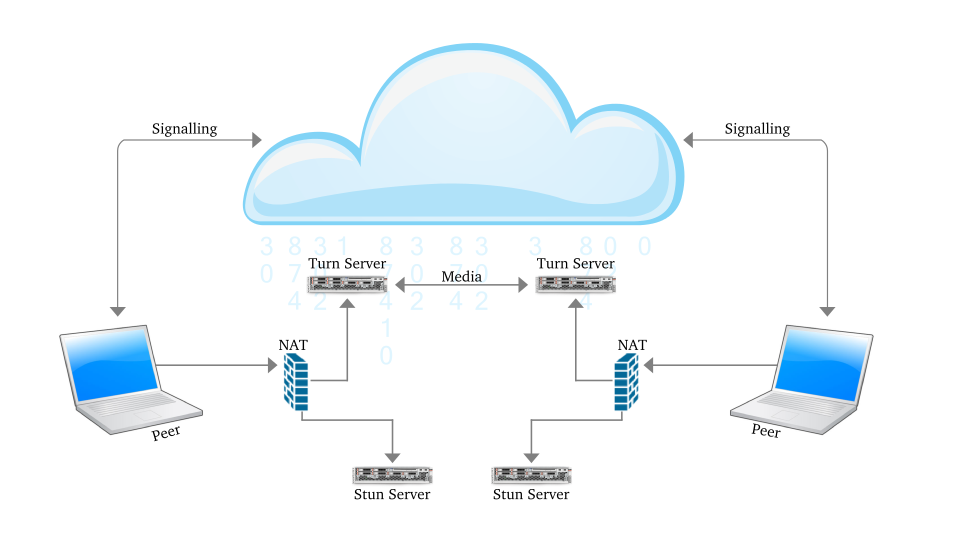
Figure 1:Communication using STUN server
Some NAT devices only allow packets from the remote peer to reach the NATed peer. Thus, a STUN fails here as the STUN server could reach the NATed peer through the server-reflexive address. These NAT devices are called symmetric NATs.
For a device to be reachable, a device behind a symmetric NAT needs to initiate and maintain a connection to a relay. Traversal Using Relays around NAT (TURN) is a protocol which is used for the communication with the relay. It is built on top of STUN. The TURN server is located outside the NAT. A NATed TURN client asks the server to allocate a public address and port and relay packets to from that address.
In simple words we can say that unlike STUN, a TURN server remains in the media path after the connection has been established. That is why the term “relay” is used to define TURN. The address which is allocated by the TURN server is called the relayed address. The TURN server tells that address to the TURN client. In every NAT case,almost the communication is possible through TURN server.
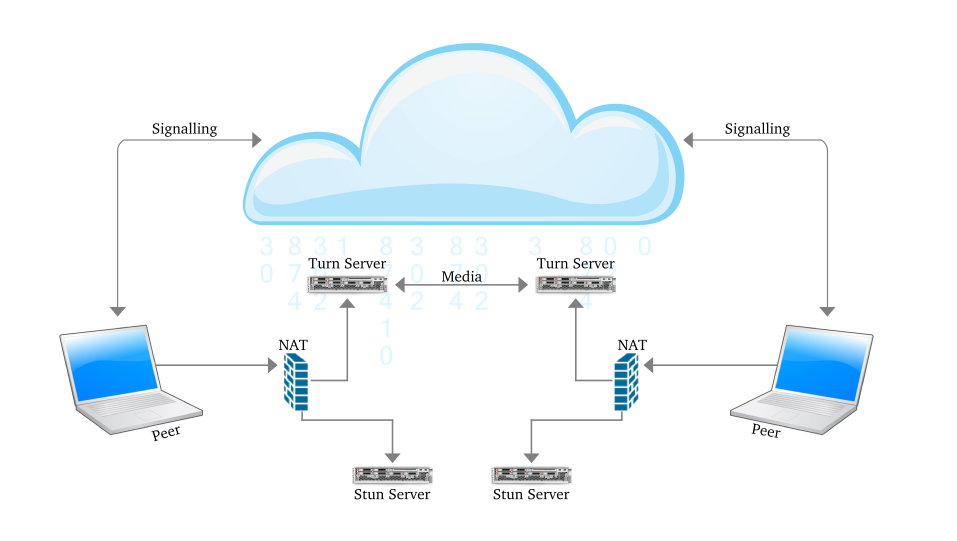
Figure 2:Communication using TURN Server
To tell the other party about these addresses ICE is used. Interactive Connectivity Establishment (ICE) has the responsibility to find the path which is best for the peers to communicate with other.
ICE first tries to make a connection using the host address obtained from a device operating system ; if connection is not established (which it will for devices behind NATs) , an external address using a STUN server is obtained by ICE, and if that also fails, traffic is routed via a TURN relay server.
In other words:
- A STUN server is used to get an external network address.
- TURN servers are used to relay traffic if direct (peer to peer) connection fails.
NOTE:-
1.Every TURN server supports STUN: a TURN server is a STUN server with added relaying functionality built in.
2.Authentication parameters are supported by TURN while STUN servers do not. There are various TURN and STUN servers are available in the market. Some are listed below but it is not necessary that are always available:-
{“url”:”stun:stun.l.google.com:19302″},
{“url”:”stun:stun1.l.google.com:19302″},
{“url”:”stun:stun2.l.google.com:19302″},
{“url”:”stun:stun3.l.google.com:19302″},
{“url”:”stun:stun4.l.google.com:19302″},
{“url”:”stun:stunserver.org”},
{“url”:”stun:stun.xten.com”},
{
“url”: “turn:numb.viagenie.ca”,
“credential”: “muazkh”,
“username”: “webrtc@live.com”
},
{
“url”: “turn:192.158.29.39:3478?transport=udp”,
“credential”: “JZEOEt2V3Qb0y27GRntt2u2PAYA=”,
“username”: ‘28224511:1379330808″
},
{
“url”: “turn:192.158.29.39:3478?transport=tcp”,
“credential”: “JZEOEt2V3Qb0y27GRntt2u2PAYA=”,
“username”: “28224511:1379330808”
}
How to check if TURN/STUN is working?
1.Wireshark
Wireshark is a powerful open source network analyzer which can be used to check the data on a network, as a medium to analyze the network traffic.
The process to be followed is:-
1)Download Wireshark by the below command
sudo apt-get install wireshark
2)Give the permission to run as root(Without this,Wireshark won’t be able to capture network traffic when you are logged in as a normal user)
sudo chmod 4711 `which dumpcap`
3)Start Wireshark by writing on the terminal
wireshark
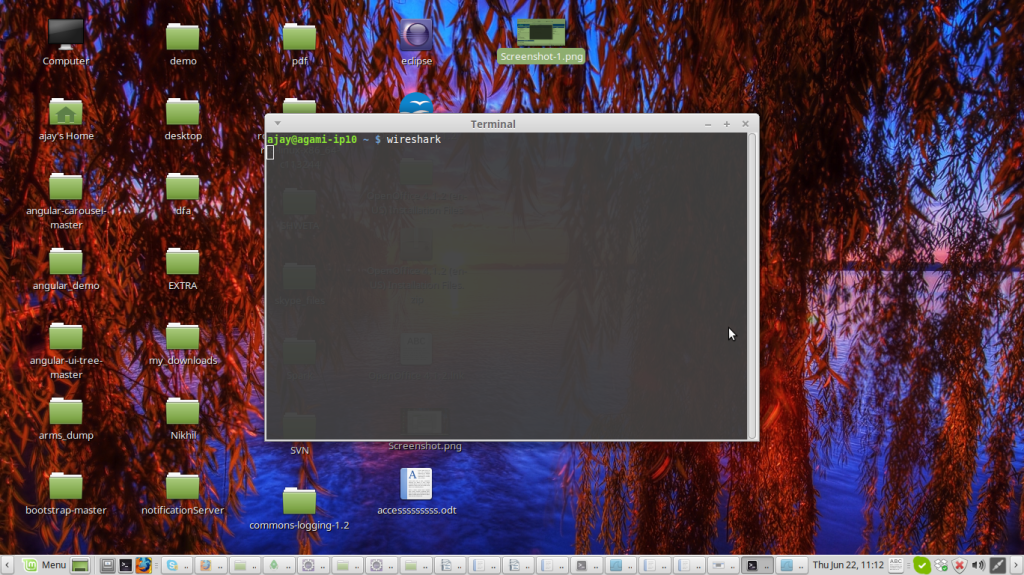
Figure 3:Screen shot to start wireshark
the below window will appear
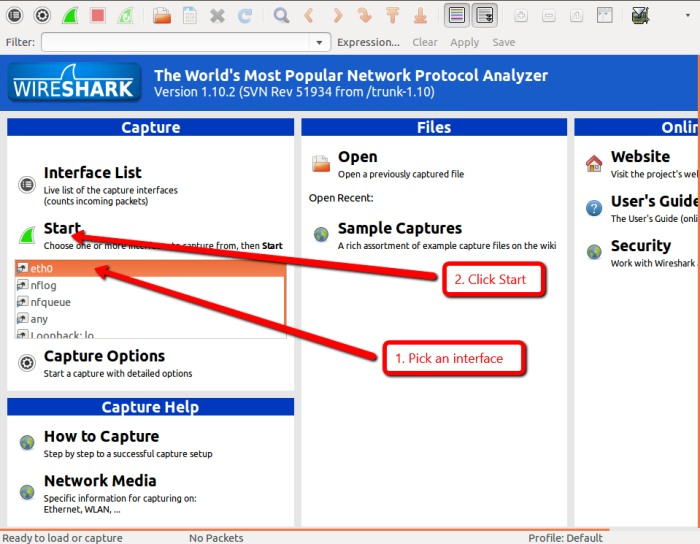
Figure 4:Main Window of WireShark
Click on the network interface you want to use to capture the data. On a wired network, it will likely be eth0. Now click Start. Wireshark will begin capturing traffic and displaying it as a color coded list in the main window.
- TCP traffic is green
- UDP packets are light blue
- ARP requests are yellow
- DNS traffic is shown in dark blue.
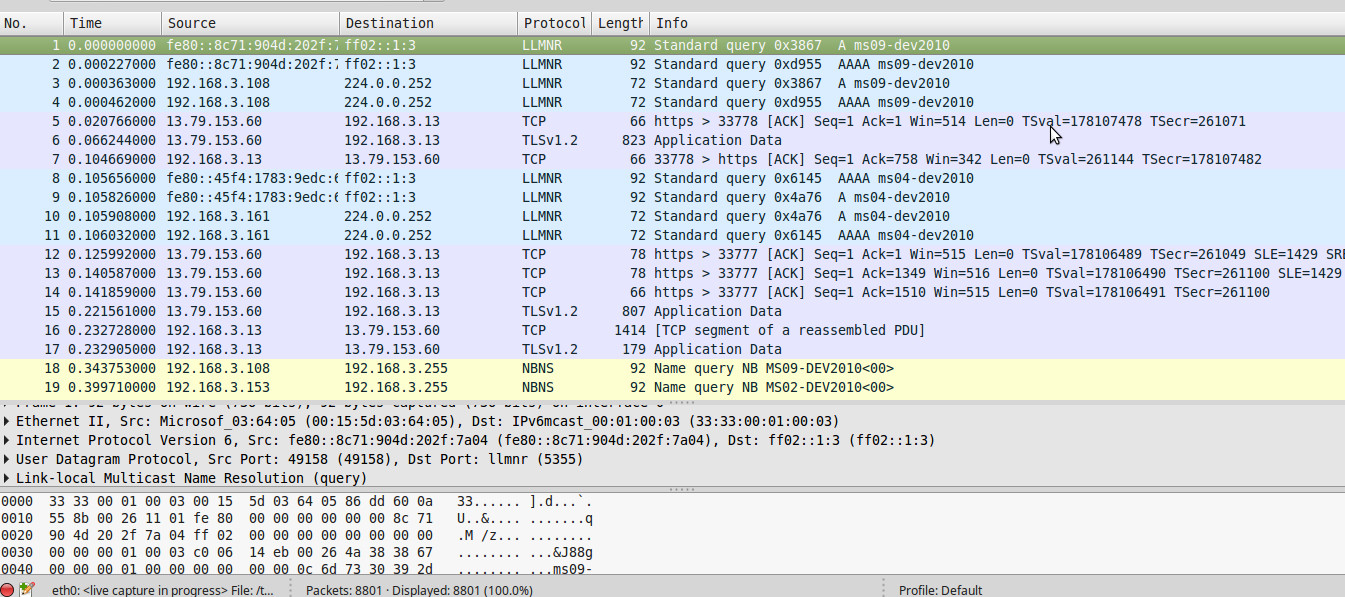
Figure 5:-Wireshark showing exchange of Packets
Wireshark can filter the type of protocol .For example, to see all the DNS related traffic that has comes from a particular host, use the filter ip.src==192.168.1.101 and dns where 192.168.1.101 is the source address you want to filter.
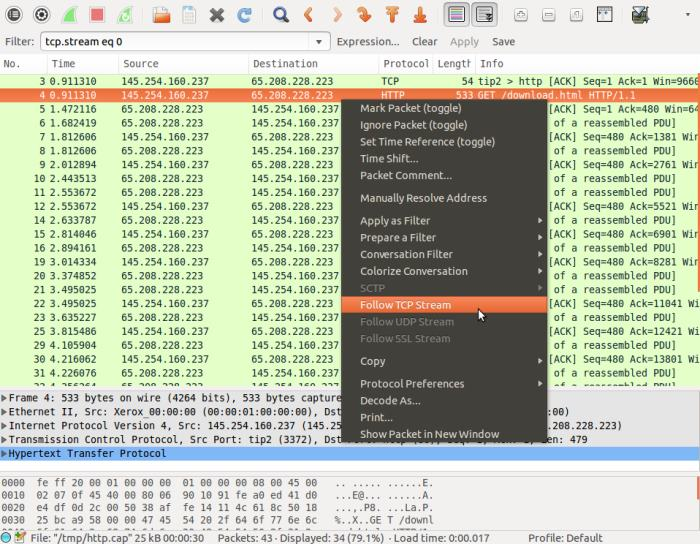 Figure 6:-Wireshark Filtering Data
Figure 6:-Wireshark Filtering Data
Wireshark has a “follow stream” option to see the conversation between two hosts. By Right clicking on any packet in the exchange and then click on “Follow TCP Stream” (or Follow UDP Stream, Follow SSL Stream depending on the protocol type). Wireshark will then show a complete copy of the conversation.
2.chrome://webRTC-internals
Open chrome://webrtc-internals while in an active WebRTC session, the API(Application Programming Interface)trace will be seen as below:
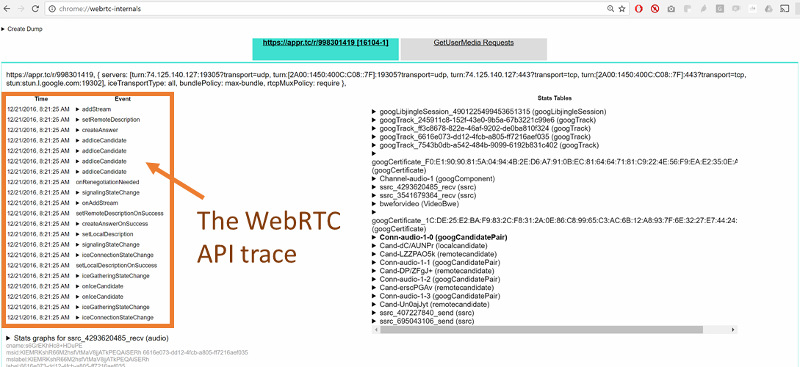
Figure 7:-WebRTC-internals showing ice candidates
You can click on any of these APIs to see its parameters.
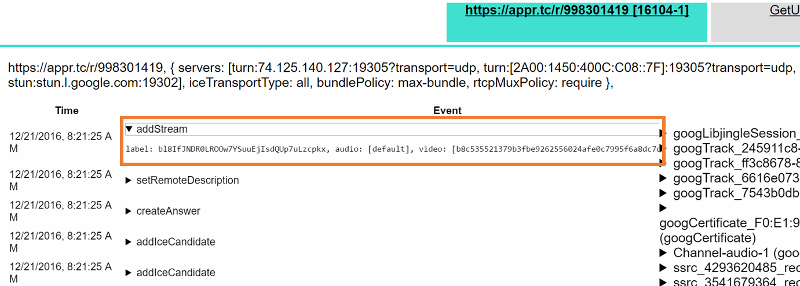
If STUN or a TURN server is being used, you should be able to see a onicecandidate() event with a candidate that has a ‘typ srflx’.
Similarly, if you use a TURN server, you need to check if you get an onicecandidate() event where the candidate has a ‘typ relay’.
If you are able to see only the host candidates you might be on a network which blocks both UDP and TCP traffic. One scenario where that might happen currently is if there is a proxy that requires authentication which is not yet supported by Chrome.
3.Trickle ice
With the help of Trickle ice we can check if our turn server is working or not.In the above figure in ICE Servers there are three boxes,which are needed to be filled .
1.STUN or TURN URI
2.TURN username
3.TURN password
In STUN or TURN URI write your turn or stun server url and click on add server,after clicking on that the you can see your turn/stun server in the box.
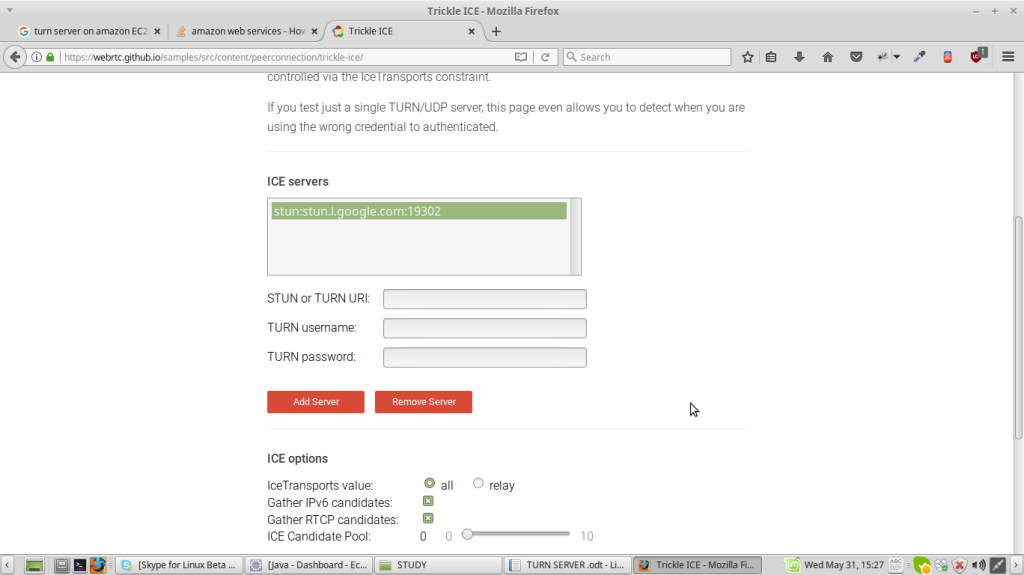
Figure 8:Trickle ICE
After that selecting on that click on Gather candidates button as shown below
you will be able to see
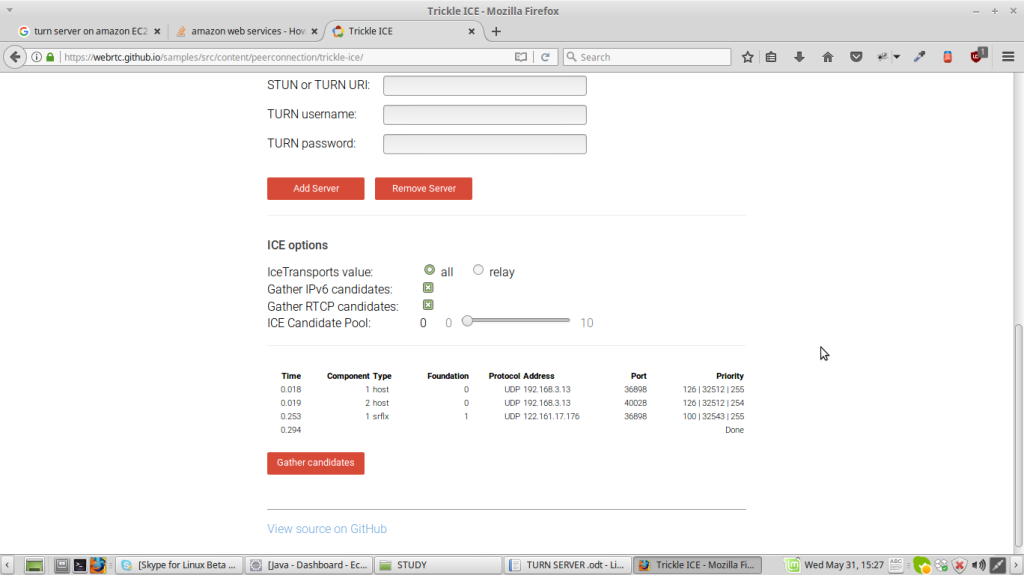
Under component type you will be able to see 1 host,1 srflx.
NOTE:-
1.If Turn server is being used then you will see relay inspite of srflx(server reflexive)
2.The username and password are to be filled should match with the username and password given in the command to run turnserver(turnserver -u <username> :<password> where -u is user credentials to be used ) otherwise you will not be able to test. And it will show not reachable.

